Financial mergers and acquisitions (M&As), especially in the fintech sector, are highly sensitive from a cybersecurity and vulnerability assessment perspective. High-profile breaches during or after acquisitions, such as the Verizon-Yahoo incident, highlight how inherited vulnerabilities can lead to major fallout.
Penetration testing plays a key role in uncovering hidden risks and securing assets during these transitions.
This article explores how to conduct penetration tests effectively throughout the M&A lifecycle to safeguard data, protect deal value, and ensure compliance.
Why pentesting is critical during fintech M&As
Penetration testing is essential during fintech M&As because vulnerabilities inherited from the acquired company often cause post-merger security weaknesses. Cybercriminals actively target organisations mid-acquisition, exploiting the security teams’ confusion and transition periods.
Security risks identified too late can jeopardise deal valuation, delay integration, or result in regulatory penalties under frameworks like FCA or GDPR. Pentesting supports stronger security measures by conducting regular security assessments. Testing ensures early detection of weaknesses and enables risk mitigation strategies critical to a successful merger.
Common security risks during M&A
Mergers and acquisitions introduce a variety of security risks, including:
- Shadow IT and undocumented services: Newly acquired firms often have hidden or unmanaged technology assets unknown to the acquirer.
- Unpatched systems or legacy applications: Outdated software with known vulnerabilities can create easy entry points for attackers.
- Poor Identity and Access Management (IAM): Overly permissive user roles or neglected accounts increase insider risk.
- Third-party dependencies and API misconfigurations: Acquisitions may inherit complex ecosystems with vulnerable vendor integrations.
- Data sprawls across multiple environments: Multiple data stores make it difficult to maintain control and visibility.
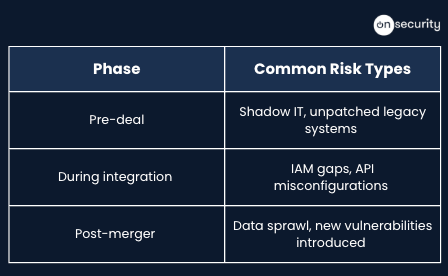
Understanding these risks and conducting penetration testing helps to comprehensively cover both legacy and newly merged assets. With a comprehensive test report, teams can implement the correct security controls to mitigate weaknesses and enhance their overall security posture.
Penetration testing best practices for M&A
Start early
Penetration testing should begin as early as possible in the due diligence phase, especially when acquiring technology-heavy or data-rich businesses. Early testing helps identify critical issues before contracts are signed, giving leverage in negotiations and more time to remediate identified vulnerabilities.
Test both companies’ assets
Conduct comprehensive external and internal penetration tests on both the acquiring and target companies. This avoids blind spots and uncovers hidden vulnerabilities within either party’s infrastructure or applications. Identifying cyber threats as early as possible is advantageous for both parties during a merger.
Map and prioritise crown-jewel assets
Identify and prioritise testing on the most sensitive assets, such as customer data repositories, core payment infrastructure, and API gateways. Focusing on these “crown jewels” ensures resources are allocated where the risk impact is highest. An ongoing established monitoring solution should be considered to protect the jewels from security flaws.
Use red teaming or adversary simulation for realism
Employ red teaming exercises or adversary simulations to mimic how real attackers might exploit weaknesses. For example, in your web application, security is crucial during the chaotic integration phase. This approach tests not just technical controls but also organisational response capabilities.
Secure CI/CD pipelines and shared tooling
Merging development environments and tooling can inadvertently expose secrets or break trust boundaries. Penetration testing should include these pipelines to prevent third-party supply chain risks and protect code integrity.
Re-test after integration
Post-merger environments often introduce new configurations or software that may create regressions. A follow-up penetration test ensures that integration has not introduced fresh security issues and reassures security teams that the network infrastructure is secure from common cyber threats.
Document findings for legal/compliance teams
Thorough documentation of penetration test results supports audit requirements and regulatory compliance. Clear reporting helps legal teams understand risks and remedial actions during due diligence and beyond. With real-time reporting, security professionals can address security flaws almost immediately to prevent unauthorised access.
How OnSecurity supports M&A pentesting
OnSecurity offers fast, reliable penetration testing tailored for fintech organisations to identify security vulnerabilities. Our experienced testing team works discreetly and efficiently under tight due diligence deadlines to deliver real-time reporting and remediation guidance, ensuring that your complete testing requirements are handled efficiently.
Penetration testing best practices during financial mergers and acquisitions are crucial for reducing risk, protecting sensitive data, and ensuring compliance with regulations. Start testing early, cover both companies’ assets, prioritise crown jewels, and re-test post-integration to safeguard your fintech M&A.




